I²R Research Highlights
Cloud Data Privacy with Homomorphic Encryption
Uploading data to the cloud poses many problems. Security risks of cloud computing have become one of the top concerns in the industry.
Most of us use some form of cloud file storage service, however, our data is not necessarily secured by these service providers. Encryption offers a way to protect our data, but we would lose the ability to use them in the cloud.
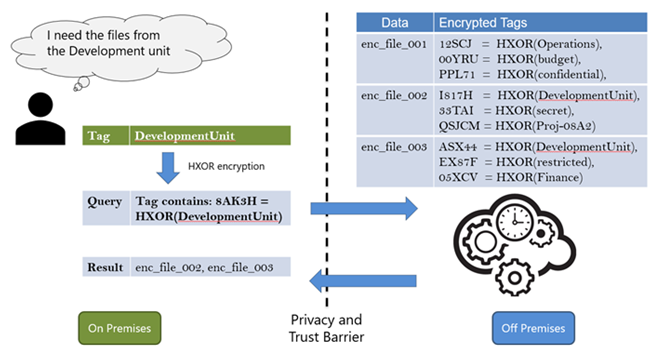
Therefore, building on their patented Searchable Encryption (SE) scheme, I2R’s Cybersecurity team and Machine Intellection team developed XORSE (now known as Privacy ENhanced Data Aggregation -PENDA).
This is an SE scheme which allows cipher texts to be compared without revealing their encrypted information. In addition, an exclusive-or homomorphic randomized masking scheme was developed to enable equality comparisons between encrypted data. Unlike other SE schemes, PENDA randomizes the encrypted queries such that the same keyword would have many different possible outputs. This property prevents third parties from identifying access patterns based on your queries as they would only see random strings being sent to the server. This scheme is extremely useful for merging multiple data using a common joining key while still preserving the privacy of the data by anonymizing the common key.
Here’s how it works:
PENDA combines deterministic AES with a random pad equipped with a secret structure to achieve randomized outputs for any keyword.

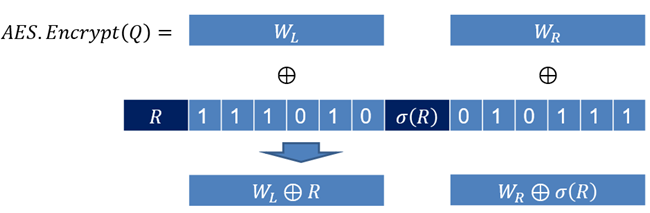
Users of the scheme generate two keys, an AES-128 key to encrypt keywords and a 64-object permutation
to imbue the random pad with some hidden structure.
Encryption of query keywords with PENDA is as follows: First, encrypt
with the deterministic AES to obtain the encrypted keyword
. Next, generate a 64-bit random bit-string
and permute its bits to get
.
Finally, we obtain the PENDA randomized encrypted keyword , where
is the bit-wise exclusive-or operation.
Checking that two PENDA ciphertexts encrypt the same keyword requires the use of the permutation . So, the server holds a copy of
, enabling it to search on encrypted keywords but does not allow queries to be generated. Two XORSE ciphertexts
encrypt the same keyword if
has the form of the structured random pad used in PENDA. We compared PENDA’s performance with the SE scheme from Song et al. 10000 records, with one encrypted keyword each, were uploaded onto a server.
The time taken for the server to find a match with the given encrypted keyword query from the client were shown in the below table. The results showed that searching with PENDA were at least 28% faster.
|
Location of the match |
Search time (ms) |
|
|
XORSE |
Song et al. |
|
|
2500 |
3.524 |
4.947 |
|
5000 |
6.984 |
9.989 |
|
7500 |
10.572 |
14.913 |
|
10000 |
13.958 |
20.036 |
|
Not present |
14.032 |
19.769 |
Further works with PENDA
Using this principle, PENDA was adapted for secure and private data aggregation, and was used by our Cybersecurity team in the Personal Data Protection Challenge 2016 where they emerged the winner.
In this competition, the system securely merged datasets without revealing the sensitive personally identifiable information needed to identify records of the same person with the PENDA searchable encryption scheme, HXOR.
Our solution collects records from participating organizations and encrypts the sensitive identifiers with HXOR. These encrypted identifiers are then used by the privacy-preserving data aggregator (PDAgg) to determine which records share the same identifier and should be grouped together.
With our solution, the privacy-preserving data collector (PDC) and the PDAgg were able to process far more records in a short time. 50,000 identifiers per second for the PDC and 1 million records each from 3 organizations in less than a minute for the PDAgg were processed by the system respectively.
As cloud storage systems become the norm in today’s IT infrastructure, our patented PENDA SE scheme offers the protection needed for your data as it is shared on these platforms.
* The A*STAR I2R researchers contributing to this research are Khin Mi Mi Aung, Benjamin Tan Hong Meng, Jestine Paul, Deng Xiao Xia (of Cybersecurity dept) and Anitha Veeramani and Saravanan Rajamanickam (of Machine intellection dept).
Papers for reference:
Shu Qin Ren, Benjamin Hong Meng Tan, Sivaraman Sundaram, Taining Wang, Khin Mi Mi Aung, Homomorphic Exclusive-Or Operation Enhance Secure Searching on Cloud Storage. CloudCom 2014: 989-994
Shu Qin Ren, Benjamin Hong Meng Tan, Yibin Ng, Khin Mi Mi Aung, Privacy-Preserved Multi-Party Data Merging with Secure Equality Evaluation. ICCCRI 2016: 34-41
Shu Qin Ren, Benjamin Hong Meng Tan, Sivaraman Sundaram, Taining Wang, Yibin Ng, Victor Chang, Khin Mi Mi Aung, Secure Searching on Cloud Storage Enhanced by Homomorphic Indexing. Future Generation Comp. Syst. 65: 102-110 (2016)
Patent found in METHOD AND SYSTEM FOR GENERATING / DECRYPTING CIPHERTEXT, AND METHOD AND SYSTEM FOR SEARCHING CIPHERTEXTS IN A DATABASE, REN Shuqin, TAN Hong Meng Benjamin, Aung Khin Mi Mi, SUNDARAM Sivaraman- US Patent 10,693,626, 2020 https://patentscope.wipo.int/search/en/detail.jsf?docId=WO2015163822
A*STAR celebrates International Women's Day

From groundbreaking discoveries to cutting-edge research, our researchers are empowering the next generation of female science, technology, engineering and mathematics (STEM) leaders.
Get inspired by our #WomeninSTEM
