Authentication & Onboarding Framework for Massive IoT Devices

Industry Challenges
Supply chain has become the new favourite target among hackers. 2021 saw a 639 million jump in cyber attacks compared to 2020, amounting to US$6 trillion in losses. From January to June 2021 alone, there were 1.51 billion IoT breaches. At the same time, it was found that 73% of companies globally are not prepared for cyber threats as hackers become more rampant and more creative in their pursuit.
Compared to typical IT systems, IoT devices have:
● 250,000x smaller memory
● 100x lower computing power
● 2000x lower bandwidth
Under this condition, most cyber-security solutions are not able to work, resulting in low or no security features. IoT devices hence, become the easiest point of attack in supply chains.
Compared to typical IT systems, IoT devices have:
● 250,000x smaller memory
● 100x lower computing power
● 2000x lower bandwidth
Under this condition, most cyber-security solutions are not able to work, resulting in low or no security features. IoT devices hence, become the easiest point of attack in supply chains.
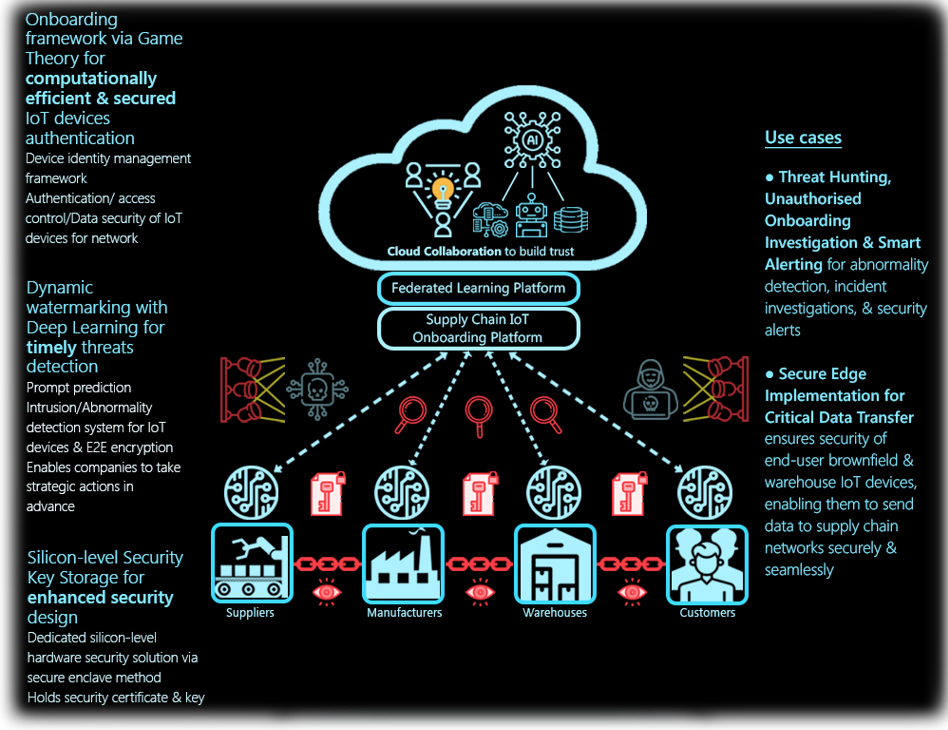
Our Solution
The Authentication & Onboarding Framework for Massive IoT Devices is designed to enhance the security of existing supply chain network (SCN) via Onboarding Framework with Game Theory and Dynamic Watermarking algorithm. Optimal for abnormality detection, protection from threats and device identity management to secure all IoT gateways and devices when applied to key areas in the supply chain.
SC4.0 hybrid cloud comprises a security architecture to boost users' confidence in the ability of people, technology and processes to create a secure digital world. Digital trust is issued to companies which have proven to provide safety, privacy, security, reliability, and data ethics with their online programs or devices.
SC4.0 hybrid cloud comprises a security architecture to boost users' confidence in the ability of people, technology and processes to create a secure digital world. Digital trust is issued to companies which have proven to provide safety, privacy, security, reliability, and data ethics with their online programs or devices.
Use Cases
• Security Intelligence & Mass Onboarding framework for “Cloud Collaboration Trust” to establish digital trust across whole supply chain
• Track & Trace Platform to facilitate monitoring and visibility of logistics operations
• Track & Trace Platform to facilitate monitoring and visibility of logistics operations
Industry Collaborations
Work in progress.
A*STAR celebrates International Women's Day

From groundbreaking discoveries to cutting-edge research, our researchers are empowering the next generation of female science, technology, engineering and mathematics (STEM) leaders.
Get inspired by our #WomeninSTEM
